
Cracking any exam requires dedication. The same is true for the Cisco CCNP Core 350-401 exam. In addition to the learning syllabus, choosing the right learning material for the exam 350-401 exam dumps is also a top priority. It can help you be more efficient. If you spend enough time, you can easily pass the 350-401 exam. Don’t let yourself be distracted during preparation.
The Pass4itSure 350-401 exam dumps help you pass the exam 100% successfully. Years of experience, professional team, 98% pass rate. Get the full exam dump question-answer click https://www.pass4itsure.com/350-401.html (total 562 Q&As).
Free Cisco 350-401 PDF | CCNP Core Exam Dumps
Free Cisco 350-401 PDF online download https://drive.google.com/file/d/1QjiI8LhKv9JbxcfDKAtgphRlKJCKmB3X/view?usp=sharing from Pass4itSure 350-401 exam dumps!
Free CCNP 350-401 ENCOR Part Of Practice Questions: Exam Experience
This is a partial incomplete CCNP 350-401 ENCOR practice question – from Pass4itSure. Of course, this is not enough. For the complete CCNP 350-401 ENCOR practice question, please visit Pass4itSure.com.
QUESTION 1
Refer to the exhibit.

An engineer must modify the access control list EGRESS to allow all IP traffic from subnet 10.1.10.0/24 to 10.1.2.0/24.
The access control list is applied in the outbound direction on router interface GigabitEthernet 0/1. Which configuration command set will allow this traffic without disrupting existing traffic flows?
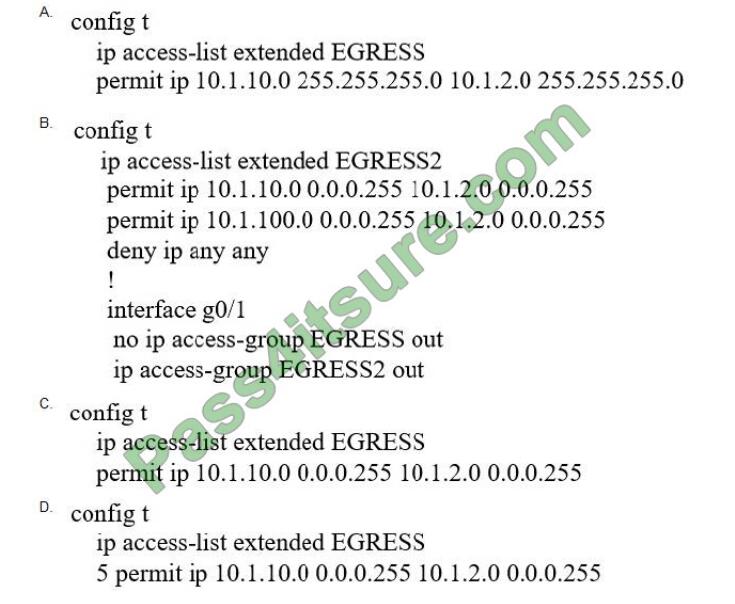
A. Option A
B. Option B
C. Option C
D. Option D
Correct Answer: D
QUESTION 2
A customer has a pair of Cisco 5520 WLCs set up in an SSO cluster to manage all APs. Guest traffic is anchored to a
Cisco 3504 WLC is located in a DM2. Which action is needed to ensure that the Eola tunnel remains in a UP state in the
event of failover on the SSO cluster?
A. Use the mobility MAC when the mobility peer is configured
B. Use the same mobility domain on all WLCs
C. Enable default gateway reachability check
D. Configure back-to-back connectivity on the RP ports
Correct Answer: B
QUESTION 3
What is the structure of a JSON web token?
A. three parts separated by dots header payload, and signature
B. header and payload
C. three parts separated by dots version header and signature
D. payload and signature
Correct Answer: A
JSON Web Token (JWT) is an open standard (RFC 7519) that defines a compact and self-contained way for securely
transmitting information between parties as a JSON object. This information can be verified and trusted because it is
digitally signed. JWTs can be signed using a secret (with the HMAC algorithm) or a public/private key pair using RSA or
ECDSA. JSON Web Tokens are composed of three parts, separated by a dot (.): Header, Payload, Signature.
Therefore, a JWT typically looks like the following:
xxxxx.yyyyy.zzzzz
The header typically consists of two parts: the type of the token, which is JWT, and the signing algorithm being used,
such as HMAC SHA256 or RSA.
The second part of the token is the payload, which contains the claims. Claims are statements about an entity (typically,
the user) and additional data. To create the signature part you have to take the encoded header, the encoded payload,
a secret, the algorithm specified in the header, and sign that.
Reference:
https://jwt.io/introduction/
https://auth0.com/docs/tokens/references/jwt-structure
QUESTION 4
Refer to the exhibit.
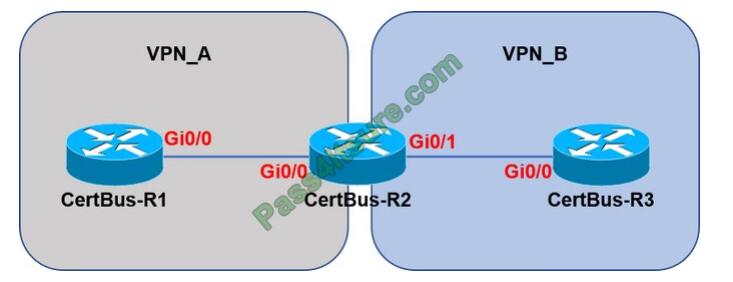
Assuming that R is a CE router, which VRF is assigned to Gi0/0 on R1?
A. V VPN_B
B. Default VRF
C. Management VRF
D. VRF VPN_A
Correct Answer: B
There is nothing special with the configuration of Gi0/0 on R1. Only the Gi0/0 interface on R2 is assigned to VRF VPN_A.
The default VRF here is similar to the global routing table concept in Cisco IOS
QUESTION 5
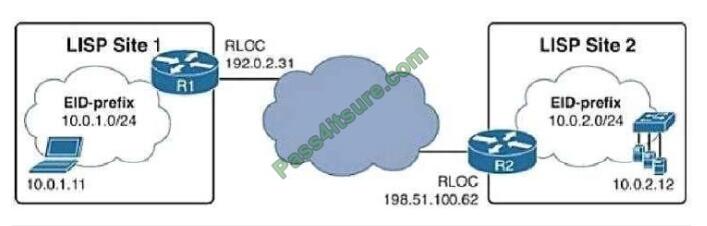
Which statement about LISP encapsulation in an EIGRP OTP implementation is true?
A. LISP learns the next hop
B. OTP uses LISP encapsulation to obtain routes from neighbors
C. OTP uses LISP encapsulation for dynamic multipoint tunneling
D. OTP maintains the LISP control plane
Correct Answer: C
The EIGRP Over the Top solution can be used to ensure connectivity between disparate EIGRP sites. This feature uses
EIGRP on the control plane and Locator ID Separation Protocol (LISP) encapsulation on the data plane to route traffic
across the underlying WAN architecture.
EIGRP is used to distribute routes between customer edge (CE) devices within
the network, and the traffic forwarded across the WAN architecture is LISP encapsulated. EIGRP OTP only uses LISP
for the data plane, EIGRP is still used for the control plane. Therefore we cannot say OTP uses LISP encapsulation for
dynamic multipoint tunneling as this requires encapsulating both data and control plane traffic -> Answer \’ OTP uses
LISP encapsulation for dynamic multipoint tunneling\’ is not correct. In OTP, EIGRP serves as the replacement for LISP
control plane protocols (therefore EIGRP will learn the next hop, not LISP -> Answer \’ LISP learns the next hop\’ is not
correct).
Instead of doing dynamic EID-to- RLOC mappings in native LISP-mapping services, EIGRP routers running
OTP over a service provider cloud create targeted sessions, use the IP addresses provided by the service provider as
RLOCs, and exchange routes as EIDs. Let\’s take an example: If R1 and R2 ran OTP to each other, R1 would learn
about the network 10.0.2.0/24 from R2 through EIGRP, treat the prefix 10.0.2.0/24 as an EID-prefix, and take the
advertising next hop 198.51.100.62 as the RLOC for this EID-prefix. Similarly, R2 would learn from R1 about the
network 10.0.1.0/24 through EIGRP, treat the prefix 10.0.1.0/24 as an EID-prefix, and take the advertising next hop
192.0.2.31 as the RLOC for this EID-prefix.
On both routers, this information would be used to populate the LISP
mapping tables. Whenever a packet from 10.0.1.0/24 to 10.0.2.0/24 would arrive at R1, it would use its LISP mapping
tables just like in ordinary LISP to discover that the packet has to be LISP encapsulated and tunneled toward
198.51.100.62, and vice versa. The LISP data plane is reused in OTP and does not change; however, the native LISP
mapping and resolving mechanisms are replaced by EIGRP. Reference: CCIE Routing and Switching V5.0 Official Cert
Guide, Volume 1, Fifth Edition
QUESTION 6
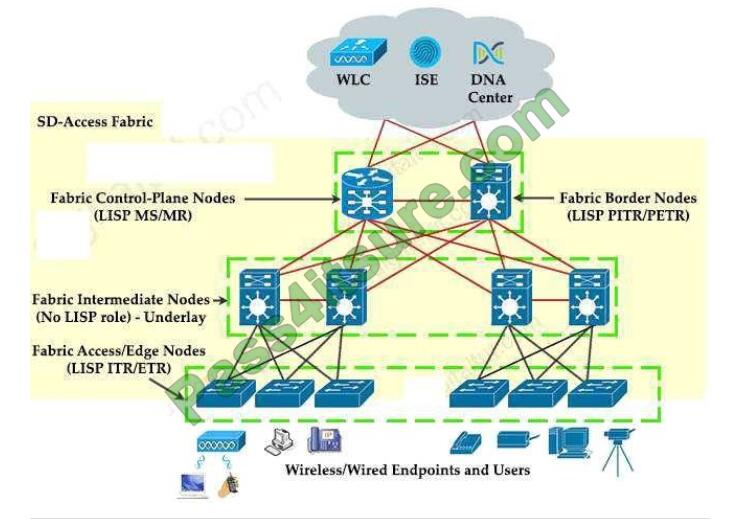
What are two device roles in Cisco SD-Access fabric? (Choose two.)
A. core switch
B. vBond controller
C. edge node
D. access switch
E. border node
Correct Answer: CE
There are five basic device roles in the fabric overlay:
+
Control plane node: This node contains the settings, protocols, and mapping tables to provide the endpoint-to-location
(EID-to-RLOC) mapping system for the fabric overlay. + Fabric border node: This fabric device (for example, core layer
device) connects external Layer 3 networks to the SDA fabric.
+
Fabric edge node: This fabric device (for example, access or distribution layer device) connects wired endpoints to the
SDA fabric.
+
Fabric WLAN controller (WLC): This fabric device connects APs and wireless endpoints to the SDA fabric.
+
Intermediate nodes: These are intermediate routers or extended switches that do not provide any sort of SD-Access
fabric role other than underlay services.
QUESTION 7
Refer to the exhibit. What is the result when a switch that is running PVST+ is added to this network?
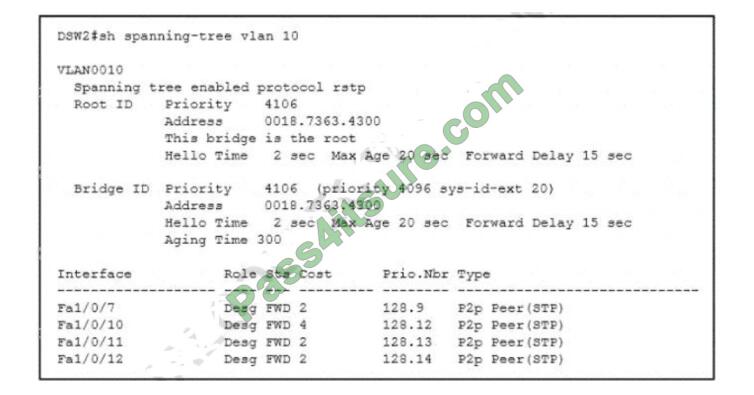
A. DSW2 operates in Rapid PVST+ and the new switch operates in PVST+
B. Both switches operate in the PVST+ mode
C. Spanning tree is disabled automatically on the network
D. Both switches operate in the Rapid PVST+ mode.
Correct Answer: A
QUESTION 8
Refer to the exhibit. Which set of commands on router r R1 Allow deterministic translation of private hosts PC1, PC2,
and PC3 to addresses in the public space?
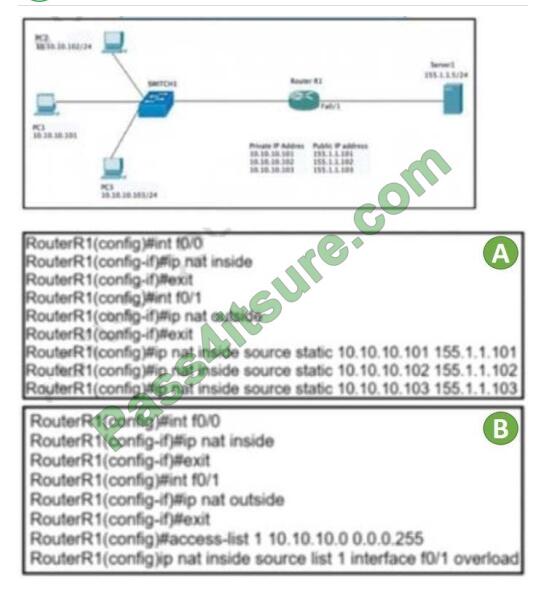
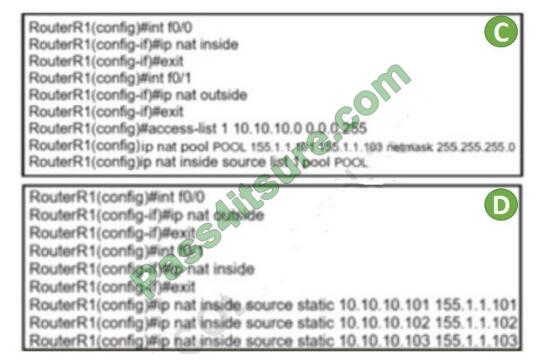
A. Option A
B. Option B
C. Option C
D. Option D
Correct Answer: A
QUESTION 9
Which configuration restricts the amount of SSH that a router accepts 100 kbps?
A. class-map match-all CoPP_SSH match access-group name CoPP_SSH ! Policy-map CoPP_SSH class CoPP_SSH
police cir 100000 exceed-action drop ! ! ! Interface GigabitEthernet0/1 ip address 209.165.200.225 255.255.255.0 ip
access-group CoPP_SSH out duplex auto speed auto media-type rj45 service-policy input CoPP_SSH ! ip access-list
extended CoPP_SSH permit tcp any any eq 22 !
B. class-map match-all CoPP_SSH match access-group name CoPP_SSH ! Policy-map CoPP_SSH class CoPP_SSH
police cir CoPP_SSH exceed-action drop ! Interface GigabitEthernet0/1 ip address 209.165.200.225 255.255.255.0 ip
access-group … out duplex auto speed auto media-type rj45 service-policy input CoPP_SSH
!
Ip access-list extended CoPP_SSH
deny TCP any eq 22
!
C. class-map match-all CoPP_SSH match access-group name CoPP_SSH ! Policy-map CoPP_SSH class CoPP_SSH
police cir 100000 exceed-action drop ! Control-plane service-policy input CoPP_SSH ! Ip access-list extended
CoPP_SSH deny tcp any any eq 22 !
D. class-map match-all CoPP_SSH match access-group name CoPP_SSH ! Policy-map CoPP_SSH class CoPP_SSH
police cir 100000 exceed-action drop ! Control-plane transit service-policy input CoPP_SSH ! Ip access-list extended
CoPP_SSH permit tcp any any eq 22 !
Correct Answer: C
CoPP protects the route processor on network devices by treating route processor resources as a separate entity with
its own ingress interface (and in some implementations, egress also). CoPP is used to police traffic that is destined to
the route processor of the router such as:
+
routing protocols like OSPF, EIGRP, or BGP.
+
Gateway redundancy protocols like HSRP, VRRP, or GLBP. + Network management protocols like telnet, SSH, SNMP,
or RADIUS.
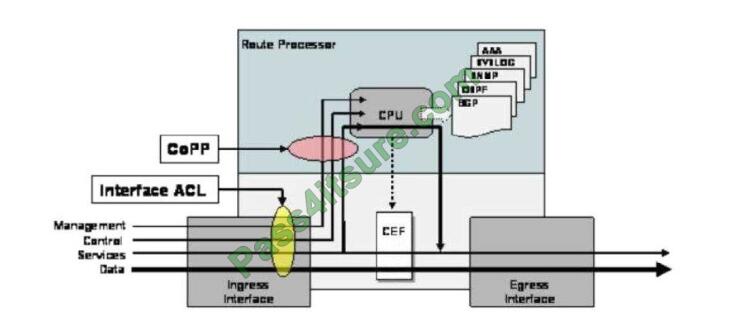
Therefore we must apply the CoPP to deal with SSH because it is in the management plane. CoPP must be put under
the “control-plane” command.
QUESTION 10
What are the two benefits of YANG? (Choose two)
A. it collects statistical constraint analysis information
B. In enforces the use of specific encoding format for NETCONF
C. in enforces configuration semantics
D. it enables multiple leaf statements to exist within a leaf-list
E. it enforces configuration constraints
Correct Answer: BE
QUESTION 11
Which IP SLA operation requires the IP SLA responder to be configured on the remote end?
A. ICMP echo
B. UDP jitter
C. CMP jitter
D. TCP connect
Correct Answer: B
Cisco IOS IP SLA Responder is a Cisco IOS Software component whose functionality is to respond to Cisco IOS IP SLA
request packets. The IP SLA source sends control packets before the operation starts to establish a connection to the
responder.
Once the control packet is acknowledged, test packets are sent to the responder. The responder inserts a
time-stamp when it receives a packet and factors out the destination processing time and adds time-stamps to the sent packets. This feature allows the calculation of unidirectional packet loss, latency, and jitter measurements with the kind of accuracy that is not possible with ping or another dedicated probe testing.
The IP SLAs responder is a component embedded in the destination Cisco device that allows the system to anticipate
and respond to IP SLAs request packets. The responder provides accurate measurements without the need for
dedicated probes.
UDP Jitter measures the delay, delay variation(jitter), corruption, misordering packet loss by generating periodic UDP
traffic. This operation always requires an IP SLA responder.
Reference: https://www.ciscolive.com/c/dam/r/ciscolive/us/docs/2017/pdf/BRKNMS-3043.pdf https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst4500/12-2/46sg/configuration/guide/Wrapper-46SG/swipsla.pdf
QUESTION 12
Based on the output below, which Python code shows the value of the “upTime” key?

A. Option A
B. Option B
C. Option C
D. Option D
Correct Answer: D
QUESTION 13
Refer to the exhibit.
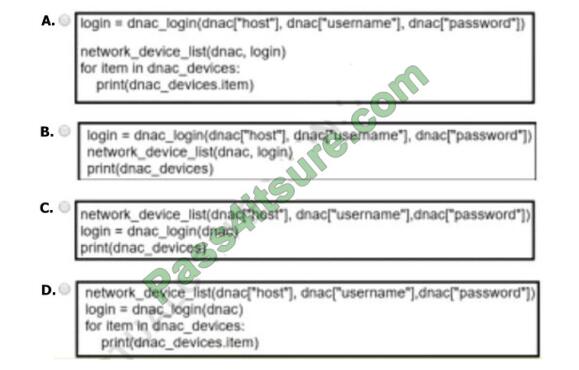
Which code results in the working python script displaying a list of network devices from the Cisco DNA Center?
A. Option A
B. Option B
C. Option C
D. Option D
Correct Answer: A
Summarize
All free content comes from real exam content! Passing the exam is not enough! Get effective complete Cisco 350-401 exam questions and answers https://www.pass4itsure.com/350-401.html (PDF +VCE). Help you pass the exam 100% successfully.
