Hey there, welcome to my latest Cisco 350-201 dumps practice space!
Are you gearing up for the 350-201 exam? Or maybe hunting for the freshest Cisco 350-201 practice questions?
I totally get it—prepping for a certification can feel like wading through an ocean of info, but no stress! I’ve got you covered with the latest July 2025 Cisco 350-201 dumps exam practice questions and answers to help you sail through the test.
This exam has evolved over the years, and whether you’re a seasoned pro or a newbie stepping into the cybersecurity world, these questions are designed to get you comfortable with the exam vibe, spot any gaps in your knowledge, and gauge your skills in real-time.
So, let’s dive in and explore the latest Cisco 350-201 exam content together!
2025 Cisco 350-201 dumps practice questions
Below are the latest updated Cisco 350-201 dumps practice questions and answers for July 2025.
| Free Materials | Free Download |
| More Cisco dumps practice questions | Cisco 350-201 PDF |
Q1:Which software development approach should be used to accomplish these goals?
An engineer is developing an application that requires frequent updates to close feedback loops and enable teams to quickly apply patches. The team wants their code updates to get to market as often as possible.
A. continuous delivery
B. continuous integration
C. continuous deployment
D. continuous monitoring
Correct Answer: A
Q2:Which step should an engineer take after receiving this alert?
An engineer received an alert of a zero-day vulnerability affecting desktop phones through which an attacker sends a crafted packet to a device, resets the credentials, makes the device unavailable, and allows a default administrator account login.
A. Initiate a triage meeting to acknowledge the vulnerability and its potential impact
B. Determine company usage of the affected products
C. Search for a patch to install from the vendor
D. Implement restrictions within the VoIP VLANS
Correct Answer: C
Q3: How are tokens authenticated when the REST API on a device is accessed from a REST API client?
Refer to the exhibit.
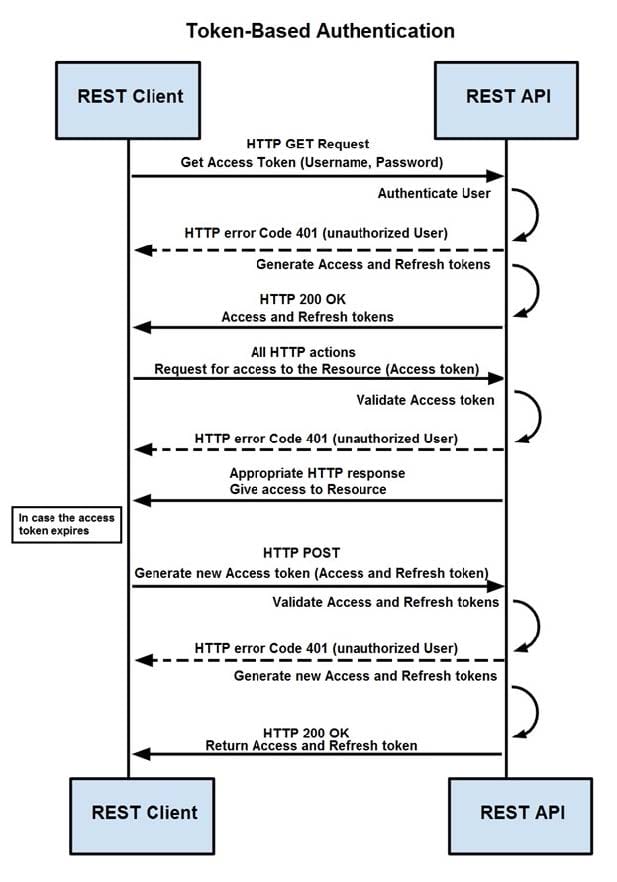
A. The token is obtained by providing a password. The REST client requests access to a resource using the access token. The REST API validates the access token and gives access to the resource.
B. The token is obtained by providing a password. The REST API requests access to a resource using the access token, validates the access token, and gives access to the resource.
C. The token is obtained before providing a password. The REST API provides resource access, refreshes tokens, and returns them to the REST client. The REST client requests access to a resource using the access token.
D. The token is obtained before providing a password. The REST client provides access to a resource using the access token. The REST API encrypts the access token and gives access to the resource.
Correct Answer: D
Q4: What results from this script?
Refer to the exhibit.
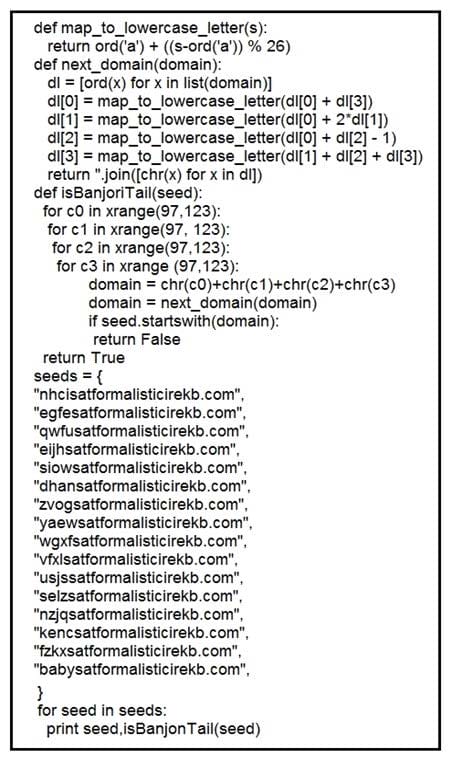
A. Seeds for existing domains are checked
B. A search is conducted for additional seeds
C. Domains are compared to seed rules
D. A list of domains as seeds is blocked
Correct Answer: B
Q5:Where does it signify that a page will be stopped from loading when a scripting attack is detected?
Refer to the exhibit.
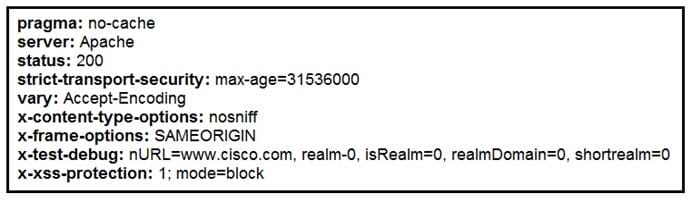
A. x-frame-options
B. x-content-type-options
C. x-xss-protection
D. x-test-debug
Correct Answer: C
Q6:What should be concluded from this report?
Refer to the exhibit.
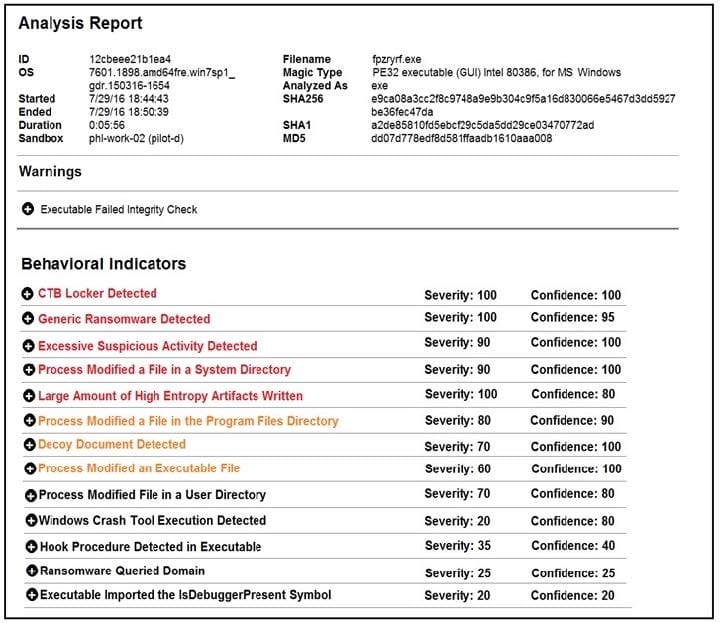
Cisco Advanced Malware Protection installed on an end-user desktop has automatically submitted a low prevalence file to the Threat Grid analysis engine for further analysis.
A. The prioritized behavioral indicators of compromise do not justify the execution of the “ransomware” because the scores do not indicate the likelihood of malicious ransomware.
B. The prioritized behavioral indicators of compromise do not justify the execution of the “ransomware” because the scores are high and do not indicate the likelihood of malicious ransomware.
C. The prioritized behavioral indicators of compromise justify the execution of the “ransomware” because the scores are high and indicate the likelihood that malicious ransomware has been detected.
D. The prioritized behavioral indicators of compromise justify the execution of the “ransomware” because the scores are low and indicate the likelihood that malicious ransomware has been detected.
Correct Answer: C
Q7:What is the next step in analyzing this attachment to allow the analyst to gather indicators of compromise?
A SOC analyst is investigating a recent email delivered to a high-value user for a customer whose network their organization monitors. The email includes a suspicious attachment titled “Invoice RE: 0004489”. The hash of the file is gathered from the Cisco Email Security Appliance. After searching Open Source Intelligence, no available history of this hash is found anywhere on the web.
A. Run and analyze the DLP Incident Summary Report from the Email Security Appliance
B. Ask the company to execute the payload for real time analysis
C. Investigate further in open source repositories using YARA to find matches
D. Obtain a copy of the file for detonation in a sandbox
Correct Answer: D
Q8:What is the next step the engineer should take to analyze this malware?
An engineer is utilizing interactive behavior analysis to test malware in a sandbox environment to see how the malware performs when it is successfully executed. A location is secured to perform reverse engineering on a piece of malware.
A. Run the program through a debugger to see the sequential actions
B. Unpack the file in a sandbox to see how it reacts
C. Research the malware online to see if there are noted findings
D. Disassemble the malware to understand how it was constructed
Correct Answer: C
Q9:What must be added to this script to receive a successful HTTP response?
An analyst received multiple alerts on the SIEM console of users that are navigating to malicious URLs. The analyst needs to automate the task of receiving alerts and processing the data for further investigations. Three variables are available from the SIEM console to include in an automation script: console_ip, api_token, and reference_set_name.
#!/usr/bin/pythonimport sysimport requests
A. {1}, {2}
B. {1}, {3}
C. console_ip, api_token
D. console_ip, reference_set_name
Correct Answer: C
Q10:Which method was used to signal ISE to quarantine the endpoints?
Refer to the exhibit.
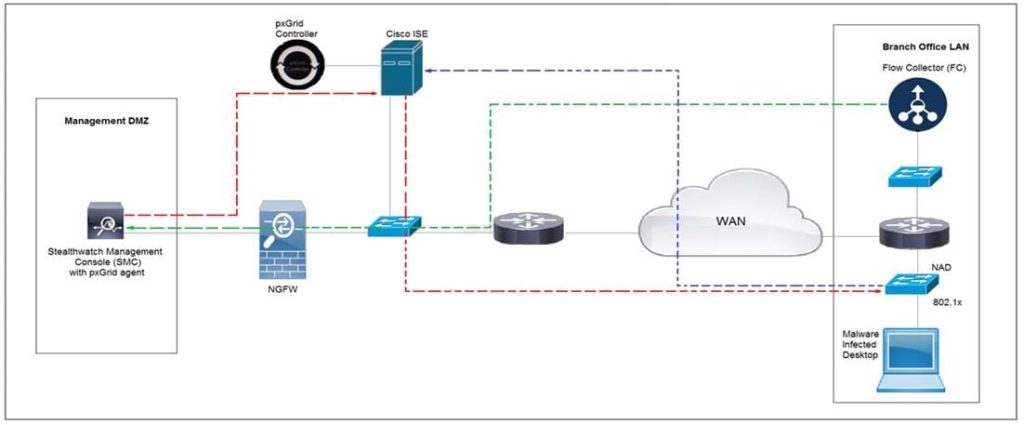
Rapid Threat Containment using Cisco Secure Network Analytics (Stealthwatch) and ISE detects the threat of malware-infected 802.1x authenticated endpoints and places that endpoint into a quarantine VLAN using Adaptive Network Control policy.
A. SNMP
B. syslog
C. REST API
D. pxGrid
Correct Answer: C
Q11:Which step should be taken to continue the investigation?
A Mac laptop user notices that several files have disappeared from their laptop documents folder. While looking for the files, the user notices that the browser history was recently cleared. The user raises a case, and an analyst reviews the network usage and discovers that it is abnormally high.
A. Run the sudo sysdiagnose command
B. Run the sh command
C. Run the w command
D. Run the who command
Correct Answer: A
Reference: https://eclecticlight.co/2016/02/06/the-ultimate-diagnostic-tool-sysdiagnose/
Q12:Which type of compromise is occurring?
Refer to the exhibit.
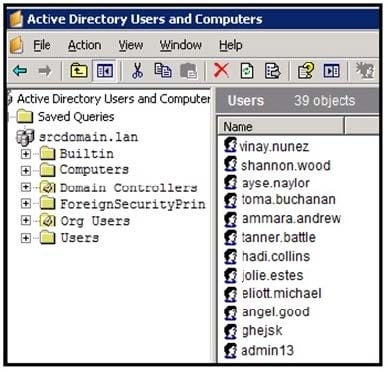
An engineer is investigating a case with suspicious usernames within the active directory. After the engineer investigates and cross-correlates events from other sources, it appears that the 2 users are privileged, and their creation date matches suspicious network traffic that was initiated from the internal network 2 days prior.
A. compromised insider
B. compromised root access
C. compromised database tables
D. compromised network
Correct Answer: D
Q13:What is the first step the analyst should take to address this incident?
A patient views information that is not theirs when they sign in to the hospital\’s online portal. The patient calls the support center at the hospital but continues to be put on hold because other patients are experiencing the same issue. An incident has been declared, and an engineer is now on the incident bridge as the CyberOps Tier 3 Analyst. There is a concern about the disclosure of PII occurring in real-time.
A. Evaluate visibility tools to determine if external access resulted in tampering
B. Contact the third-party handling provider to respond to the incident as critical
C. Turn off all access to the patient portal to secure patient records
D. Review system and application logs to identify errors in the portal code
Correct Answer: C
Q14:What is idempotence?
A. the assurance of system uniformity throughout the whole delivery process
B. the ability to recover from failures while keeping critical services running
C. the necessity of setting maintenance of individual deployment environments
D. the ability to set the target environment configuration regardless of the starting state
Correct Answer: A
Q15:What is the next step the engineer should take to investigate this case?
Employees report computer system crashes within the same week. An analyst is investigating one of the computers that crashed and discovers multiple shortcuts in the system\’s startup folder. It appears that the shortcuts redirect users to malicious URLs.
A. Remove the shortcut files
B. Check the audit logs
C. Identify affected systems
D. Investigate the malicious URLs
Correct Answer: C
That’s it for the free share of the latest July 2025 Cisco 350-201 exam dumps and answers!
Prepping for the 350-201 CBRCOR exam might feel like running a marathon, but with these Cisco 350-201 practice questions, you’re already a step ahead. Of course, the full set of exam questions and answers goes way beyond this—head over to https://www.pass4itsure.com/350-201.html to grab all 139 of the latest questions and answers. Dive in, test your skills, and don’t sweat the mistakes—that’s how you learn!
If you’ve got your sights set on crushing this exam, then grab those questions, hit the books, and get ready to shine!
Cisco 350-201 FAQs 2025
When will the second exam for the Cisco Certified CyberOps Professional certification be available?
The second exam is already available. Candidates can choose either 300-215 CBRFIR (focused on forensic analysis and incident response) or 300-220 CBRTHD (focused on threat hunting and defense) as the concentration exam.
Will passing the 350-201 exam recertify my associate-level certification?
Yes, passing the 350-201 (a professional-level core exam) will recertify your associate-level certification (e.g., Cisco Certified CyberOps Associate), provided it’s completed before the associate certification expires. Cisco certifications are valid for three years, and you can recertify by advancing to a higher level.
What are the prerequisites for the 350-201 exam?
There are no formal prerequisites, but Cisco recommends having an associate-level certification (e.g., Cisco Certified CyberOps Associate) or equivalent knowledge in cybersecurity operations.
What are the career benefits of obtaining the 350-201 certification?
This certification validates advanced cybersecurity operations skills, boosting job opportunities and salary potential, especially for roles like SOC analysts, incident response specialists, and security engineers.
Should I take the associate-level exam (200-201) first or go straight for the professional-level exam (350-201)?
If you’re new to cybersecurity fundamentals, start with the associate-level exam (200-201 CBROPS), which covers security monitoring, analysis, and response basics. If you have relevant experience, you can go straight for the 350-201, but ensure you’re solid on associate-level knowledge.
What’s the difference between the CBRFIR and CBRTHD concentration exams?
CBRFIR (300-215) focuses on forensic analysis and incident response, ideal for those interested in investigation and response. CBRTHD (300-220) focuses on threat hunting and defense, suited for those interested in proactively identifying and mitigating threats. Choose based on your career goals.
Is the Cisco Certified CyberOps Professional certification worth it for career growth?
Absolutely, this certification is highly valued in the cybersecurity field, recognized globally by employers, and can enhance career opportunities and salary potential, especially for senior roles in SOCs, incident response teams, and more.
Are the Cisco 350-201 dumps practice questions useful?
Yes, these are proven, authentic, and effective practice materials. They currently boast a high pass rate of 97.9%, and Pass4itsure regularly updates the materials to ensure they’re always ready for download and use.
