
No bad intentions, just to help you win the (CEHv12) exam. How to do it, you must be curious. Don’t worry, Pass4itSure has released a new 312-50V12 dumps (a new study quiz that includes all the exam content), and if you practice hard, you can win the 312-50V12 exam very well.
What you need to do: Download the Pass4itSure 312-50v12 dumps PDF or VCE https://www.pass4itsure.com/312-50v12.html and do the 528+ practice questions.
The EC-Council Certified Ethical Hacker (CEHv12) 312-50V12 exam is a certification exam that measures candidates’ knowledge and skills in cybersecurity.
Where the 312-50V12 exam is difficult?
In order to help you with the 312-50V12 exam, I have sorted out the difficulties of the exam:
Complex technical jargon:
This can be confusing for some test takers.
Familiar with various tools:
Such as vulnerability scanners, network sniffers, port scanners, password cracking tools, etc., there are many and easy to confuse.
Master network attack techniques:
Including denial of service attacks, SQL injection attacks, phishing, etc., candidates need to master the principles and countermeasures of these attack techniques.
The exam requires candidates to understand various network attack techniques including denial of service attacks, SQL injection attacks, phishing, etc., and candidates need to master the principles and countermeasures of these attack techniques.
Familiarity with various cybersecurity standards and regulations:
such as ISO 27001, HIPAA, GDPR, etc., requires in-depth knowledge.
A large amount of exam content:
The exam content is very extensive and requires candidates to put in a lot of time and effort to study and prepare for the exam.
What are the specific ways to deal with the difficulties of the 312-50V12 exam?
As a candidate, you should be well prepared, familiar with the content of the exam and technical terms, master various security tools and attack techniques, and understand cybersecurity standards and regulations.
At the same time, you should use the latest 312-50v12 dumps (which can be updated by Pass4itSure) to practice the exam questions to ensure excellent results.
Next, Old Rules, share the latest 312-50v12 exam questions (free)
Come and take the 312-50V12 practice test and improve your ability.
Question 1:
In an attempt to damage the reputation of a competitor organization, Hailey, a professional hacker, gathers a list of employee and client email addresses and other related information by using various search engines, social networking sites, and web-spidering tools. In this process, she also uses an automated tool to gather a list of words from the target website to further perform a brute-force attack on the previously gathered email addresses.
What is the tool used by Hailey for gathering a list of words from the target website?
A. Shadowsocks
B. CeWL
C. Psiphon
D. Orbot
Correct Answer: B
Question 2:
Which of the following allows attackers to draw a map or outline the target organization\’s network infrastructure to know about the actual environment that they are going to hack?
A. Enumeration
B. Vulnerability analysis
C. Malware analysis
D. Scanning networks
Correct Answer: D
Question 3:
Null sessions are unauthenticated connections (not using a username or password.) to an NT or 2000 system. Which TCP and UDP ports must you filter to check null sessions on your network?
A. 137 and 139
B. 137 and 443
C. 139 and 443
D. 139 and 445
Correct Answer: D
Question 4:
John, a disgruntled ex-employee of an organization, contacted a professional hacker to exploit the organization. In the attack process, the professional hacker Installed a scanner on a machine belonging to one of the vktims and scanned several machines on the same network to Identify vulnerabilities to perform further exploitation. What is the type of vulnerability assessment tool employed by John in the above scenario?
A. Proxy scanner
B. Agent-based scanner
C. Network-based scanner
D. Cluster scanner
Correct Answer: C
Network-based scanner
A network-based vulnerability scanner, in simplistic terms, is the process of identifying loopholes in a computer\’s network or IT assets, which hackers and threat actors can exploit. By implementing this process, one can successfully identify their organization\’s current risk(s).
This is not where the buck stops; one can also verify the effectiveness of your system\’s security measures while improving internal and external defenses. Through this review, an organization is well
equipped to take an extensive inventory of all systems, including operating systems, installed software, security patches, hardware, firewalls, anti-virus software, and much more.
Agent-based scanner
Agent-based scanners make use of software scanners on each and every device; the results of the scans are reported back to the central server. Such scanners are well-equipped to find and report on a range of vulnerabilities.
NOTE:
This option is not suitable for us, since for it to work, you need to install a special agent on each computer before you start collecting data from them.
Question 5:
You are programming a buffer overflow exploit and you want to create a NOP sled of 200 bytes in the program exploit.c
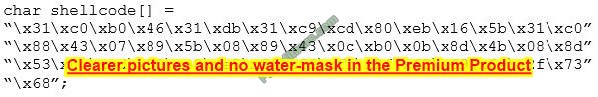
What is the hexadecimal value of NOP instruction?
A. 0x60
B. 0x80
C. 0x70
D. 0x90
Correct Answer: D
Question 6:
Which of the following tools is used to analyze the files produced by several packet-capture programs such as tcpdump, WinDump, Wireshark, and EtherPeek?
A. tcptrace
B. Nessus
C. OpenVAS
D. tcptraceroute
Correct Answer: A
Question 7:
During a Xmas scan, what indicates a port is closed?
A. No return response
B. RST
C. ACK
D. SYN
Correct Answer: B
Question 8:
Which Nmap switch helps evade IDS or firewalls?
A. -n/-R
B. -0N/-0X/-0G
C. -T
D. -D
Correct Answer: C
Question 9:
An attacker redirects the victim to malicious websites by sending them a malicious link by email. The link appears authentic but redirects the victim to a malicious web page, which allows the attacker to steal the victim\’s data. What type of attack is this?
A. Phishing
B. Vlishing
C. Spoofing
D. DDoS
Correct Answer: A
https://en.wikipedia.org/wiki/Phishing Phishing is a type of social engineering attack often used to steal user data, including login credentials and credit card numbers. It occurs when an attacker, masquerading as a trusted entity, dupes a victim into opening an email, instant message, or text message. The recipient is then tricked into clicking a malicious link, which can lead to the installation of malware, the freezing of the system as part of a ransomware attack, or the revealing of sensitive information. An attack can have devastating results.
For individuals, this includes unauthorized purchases, the stealing of funds, or identity theft. Moreover, phishing is often used to gain a foothold in corporate or governmental networks as a part of a larger attack, such as an advanced persistent threat (APT) event. In this latter scenario, employees are compromised in order to bypass security perimeters, distribute malware inside a closed environment, or gain privileged access to secured data.
An organization succumbing to such an attack typically sustains severe financial losses in addition to declining market share, reputation, and consumer trust. Depending on the scope, a phishing attempt might escalate into a security incident from which a business will have a difficult time recovering.
Question 10:
Kate dropped her phone and subsequently encountered an issue with the phone\’s internal speaker. Thus, she is using the phone\’s loudspeaker for phone calls and other activities. Bob, an attacker, takes advantage of this vulnerability and secretly exploits the hardware of Kate\’s phone so that he can monitor the loudspeaker\’s output from data sources such as voice assistants, multimedia messages, and audio files by using a malicious app to breach speech privacy. What is the type of attack Bob performed on Kate in the above scenario?
A. Man-in-the-disk attack
B. aLTEr attack
C. SIM card attack
D. Spearphone attack
Correct Answer: D
Question 11:
What is a NULL scan?
A. A scan in which all flags are turned off
B. A scan in which certain flags are off
C. A scan in which all flags are on
D. A scan in which the packet size is set to zero
E. A scan with an illegal packet size
Correct Answer: A
Question 12:
You are a penetration tester and are about to perform a scan on a specific server. The agreement that you signed with the client contains the following specific condition for the scan: “The attacker must scan every port on the server several times using a set of spoofed sources IP addresses. ” Suppose that you are using Nmap to perform this scan. What flag will you use to satisfy this requirement?
A. The -A flag
B. The -g flag
C. The -f flag
D. The -D flag
Correct Answer: D
flags -source-port and -g are equivalent and instruct Nmap to send packets through a selected port. this option is used to try to cheat firewalls whitelisting traffic from specific ports. the following example can scan the target from port twenty to ports eighty, 22, 21,23 and 25 sending fragmented packets to LinuxHint.
Question 13:
which of the following protocols can be used to secure an LDAP service against anonymous queries?
A. SSO
B. RADIUS
C. WPA
D. NTLM
Correct Answer: D
Question 14:
What would be the purpose of running “wget 192.168.0.15 -q -S” against a web server?
A. Performing content enumeration on the webserver to discover hidden folders
B. Using wget to perform banner grabbing on the webserver
C. Flooding the web server with requests to perform a DoS attack
D. Downloading all the contents of the web page locally for further examination
Correct Answer: B
-q, –quiet quiet (no output) -S, –server-response print server response
Question 15:
Gilbert, a web developer, uses a centralized web API to reduce complexity and increase the Integrity of updating and changing data. For this purpose, he uses a web service that uses HTTP methods such as PUT. POST. GET. and DELETE can improve the overall performance, visibility, scalability, reliability, and portability of an application. What is the type of web-service API mentioned in the above scenario?
A. JSON-RPC
B. SOAP API
C. RESTful API
D. REST API
Correct Answer: C
*REST is not a specification, tool, or framework, but instead is an architectural style for web services that serve as a communication medium between various systems on the web. *RESTful APIs, which are also known as RESTful services, are designed using REST principles and HTTP communication protocols RESTful is a collection of resources that use HTTP methods such as PUT, POST, GET, and DELETE RESTful API: RESTful API is a RESTful service that is designed using REST principles and HTTP communication protocols.
RESTful is a collection of resources that use HTTP methods such as PUT, POST, GET, and DELETE. RESTful API is also designed to make applications independent to improve the overall performance, visibility, scalability, reliability, and portability of an application.
APIs with the following features can be referred to as RESTful APIs: o Stateless: The client end stores the state of the session; the server is restricted to save data during the request processing o Cacheable: The client should save responses (representations) in the cache. This feature can enhance API performance pg. 1920 CEHv11 manual.
https://cloud.google.com/files/apigee/apigee-web-api-design-the-missing-link-ebook.pdf
Conclusion:
If you want to win the 312-50v12 exam, preparation is essential, and the latest 312-50v12 dumps are essential, come and download the complete 312-50v12 dumps https://www.pass4itsure.com/312-50v12.html
Practice, in practice, good luck with the exam!
