With the updated 350-701 dumps, you can successfully pass the Implementing and Operating Cisco Security Core Technologies (SCOR) exam.
We have updated the 350-701 dumps with 492+ new practice questions and answers to help you successfully prepare, pass exams and achieve high scores.
Pass4itSure will help you, Download Cisco 350-701 Dumps: https://www.pass4itsure.com/350-701.html to get the best results on the 350-701 dumps updated 2022 exam questions in the 350-701 exam.

Of course, before downloading, we have prepared a free dumps Q&A for you, you can try it first:
1. Which two are valid suppression types on a Cisco Next-Generation Intrusion Prevention System? (Choose two)
A. Port
B. Rule
C. Source
D. Application
E. Protocol
Correct Answer: BC
2. Which functions of an SDN architecture require southbound APIs to enable communication?
A. SDN controller and the network elements
B. management console and the SDN controller
C. management console and the cloud
D. SDN controller and the cloud
Correct Answer: A
The Southbound API is used to communicate between Controllers and network devices
3. Which two deployment modes does the Cisco ASA FirePower module support? (Choose two)
A. transparent mode
B. routed mode
C. inline mode
D. active mode
E. passive monitor-only mode
Correct Answer: CD
Reference: https://www.cisco.com/c/en/us/td/docs/security/asa/asa92/asdm72/firewall/asa-firewall-asdm/modulessfr.html
4. Refer to the exhibit.
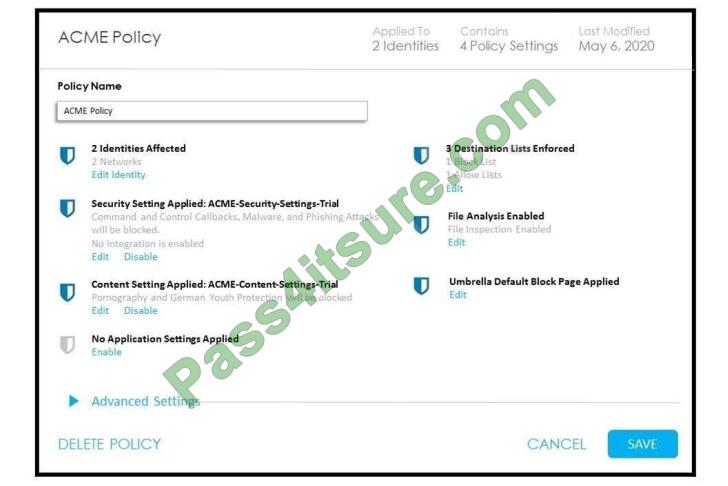
How does Cisco Umbrella manage traffic that is directed toward risky domains?
A. Traffic is managed by the application settings, unhandled, and allowed.
» Read more about: 350-701 Dumps Updated Great Help In Passing The Cisco SCOR Exam »








