Use our 350-401 dumps (r 9.27) to prepare for the Cisco CCNP 350-401 exam. Our new 350-401 dumps (r 9.27) contains 866 practice questions and answers to ensure you’re ready.
Pass4itSure 350-401 dumps (r 9.27) best 350-401 ECOR exam preparation materials. Go to the webpage for a 350-401 dumps: https://www.pass4itsure.com/350-401.html (latest).
Need to know the basics of the 350-401 exam?

To pass the 350-401 exam, understanding the basics of the exam is the first step. Therefore, it is necessary.
The 350-401 exam is also known as the 350-401 ENCOR. It requires you to answer 100 ± questions in two hours and get 750-850 out of 1000 points to pass. It costs $400 to take the exam.
Passing the 350-401 exam is closely linked to the following certifications:
- CCNP Enterprise (CCNP Enterprise Core Exam)
- CCIE Enterprise Infrastructure (CCIE Enterprise Infrastructure Qualifying Exam)
- CCIE Enterprise Wireless (CCIE Enterprise Wireless Qualifying Exam)
How do I prepare for the Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR) exam?
Pass the 350-401 exam, how to prepare is important. You can use Pass4itSure 350-401 dumps (r 9.27) to prepare for the exam. It has the latest 350-401 exam practice questions that will help you win exams easily.
What are the learning resources for the Cisco 350-401 exam?
- Implementing Cisco Enterprise Network Core Technologies (ENCOR)
- ENCOR training videos
- ENCOR study materials
……
There are more, welcome to add.
Where are the free valid 350-401 ECOR exam preparation materials?
This blog provides you with free Cisco 350-401 ECOR exam preparation materials.
You can download the free 350-401 exam question: https://drive.google.com/file/d/1tkPwTavFjjXlt4gzLWBvpvUf9auk-Xlu/view?usp=sharing at [google drive].
Or read the online 350-401 exam questions directly below.
Cisco 350-401 Free Dumps: New 350-401 ENCOR Questions Test:
NEW QUESTION 1
What is the API keys option for REST API authentication?
A. a predetermined string that is passed from client to server
B. a one-time encrypted token
C. a username that is stored in the local router database
D. a credential that is transmitted unencrypted
Correct Answer: A
In REST API Security – API keys are widely used in the industry and became some sort of standard, however, this
the method should not be considered a good security measure.
API Keys were created as somewhat of a fix to the early authentication issues of HTTP Basic Authentication and other
such systems. In this method, a unique generated value is assigned to each first-time user, signifying that the user is
known. When the user attempts to re-enter the system, their unique key (sometimes generated from their hardware
combination and IP data, and other times randomly generated by the server which knows them) is used to prove that
they’re the same user as before.
Reference: https://blog.restcase.com/4-most-used-rest-api-authentication-methods/
NEW QUESTION 2
Refer to the exhibit.

An engineer has configured an IP SLA for UDP echo\\’s. Which command is needed to start the IP SLA to test every 30
seconds and continue until stopped?
A. IP SLA schedule 100 start-time now life forever
B. IP SLA schedule 30 start-time now life forever
C. IP SLA schedule 100 start-time now life 30
D. IP SLA schedule 100 life forever
Correct Answer: A
NEW QUESTION 3
In a Cisco SD-Access solution, which protocol is used by an extended node to connect to a single edge node?
A. VXLAN
B. IS-IS
C. 802 1Q
D. CTS
Correct Answer: C
SD-Access Extended Nodes provide the ability to extend the enterprise network by providing connectivity to non-carpeted spaces of an enterprise – commonly called the Extended Enterprise. This allows network connectivity and management of IoT devices and the deployment of traditional enterprise end devices in outdoor and non-carpeted environments such as distribution centers, warehouses, or Campus parking lots.
This feature extends consistent, policy-based automation to Cisco Industrial Ethernet, Catalyst 3560-CX Compact, and
Digital Building Series switches and enables segmentation for user endpoints and IoT devices connected to these
nodes.
Using Cisco DNA Center automation, switches in the extended node role are onboarded to their connected edge node
using an 802.1Q trunk over an EtherChannel with one or multiple physical link members. Extended nodes are
discovered using zero-touch Plug-and-Play.
NEW QUESTION 4
How does a fabric AP fit in the network?
A. It is in local mode and must be connected directly to the fabric border node
B. It is in FlexConnect mode and must be connected directly to the fabric edge switch.
C. It is in FlexConnect mode and must be connected directly to the fabric border node
D. It is in local mode and must be connected directly to the fabric edge switch.
Correct Answer: D
NEW QUESTION 5
Refer to the exhibit.
During deployment, a network engineer notices that voice traffic is not being tagged correctly as it traverses the
network. Which COS to the DSCP map must be modified to ensure that voice traffic is treated properly?
A. COS of 5 to DSCP 46
B. COS of 7 to DSCP 48
C. COS of 6 to DSCP 46
D. COS of 3 to DSCP of 26
Correct Answer: A
NEW QUESTION 6
An engineer must configure a router to leak routes between two VRFs Which configuration must the engineer apply?
A. IP access-list extended ACL-to-red permit IP any 10.1.1.0 0.0.0.255 route-map rm-to-red permit 10 match IP address 50
IP vrf RED rd 1:1 import ipv4 unicast map rm-to-red
B. IP access-list extended ACL-to-red permit IP 10.1.1.0 0.0.0.255 any route-map rm-to-red permit 10 match IP address
ACL-to-red ip vrf RED rd 1:1 import ipv4 unicast route-map ACL-to-red
C. IP access-list extended ACL-to-red permit IP 10.1.1.0 0.0.0.256 any route-map rm-to-red permit 10 match IP address
ACL-to-red ip vrf RED rd 1:1 import ipv4 unicast map rm-to-red
D. IP access-list extended ACL-to-red permit IP 10.1.1.0 0.0.0.265 any route-map rm-to-red permit 10 match IP address acl-to-red IP vrf RED rd 1:1 import ipv4 unicast ACL-to-red
Correct Answer: D
NEW QUESTION 7
Which two statements about AAA authentication are true? (Choose two)
A. RADIUS authentication queries the router`s local username database
B. TACACS+ authentication uses an RSA server to authenticate users
C. Local user names are case-insensitive
D. Local authentication is maintained on the router
E. KRB5 authentication disables user access when an incorrect password is entered
Correct Answer: DE
NEW QUESTION 8
An engineer measures the Wi-Fi coverage at a customer site. The RSSI values are recorded as follows:
Location A: -72 dBm Location B: -75 dBm Location C: -65 dBm Location D: -80 dBm
Which two statements does the engineer use to explain these values to the customer? (Choose two)
A. The signal strength at location B is 10 dB better than at location C
B. Location D has the strongest RF signal strength.
C. The signal strength at location C is too weak to support web surfing.
D. The RF signal strength at location B is 50% weaker than at location A
E. The RF signal strength at location C is 10 times stronger than at location B
Correct Answer: DE
NEW QUESTION 9
Refer to the exhibit.
Which password allows access to line con 0 for a username of “Tommy” under normal operation?
A. Cisco
B. local
C. 0 Cisco
D. Tommy
Correct Answer: A
In this question, there are two different passwords for user “Tommy”:
+
In the TACACS+ server, the password is “Tommy”
+
In the local database of the router, the password is “Cisco”.
From the line “login authentication local” we know that the router uses the local database for authentication so the
password should be “Cisco”.
Note: “… password 0 …” here means unencrypted password.
NEW QUESTION 10
In a fabric-enabled wireless network, which device is responsible for maintaining the endpoint ID database?
A. fabric border node
B. fabric edge node
C. fabric wireless controller
D. control plane node
Correct Answer: D
NEW QUESTION 11
A network engineer configures a new GRE tunnel and enters the show run command. What does the output verify?
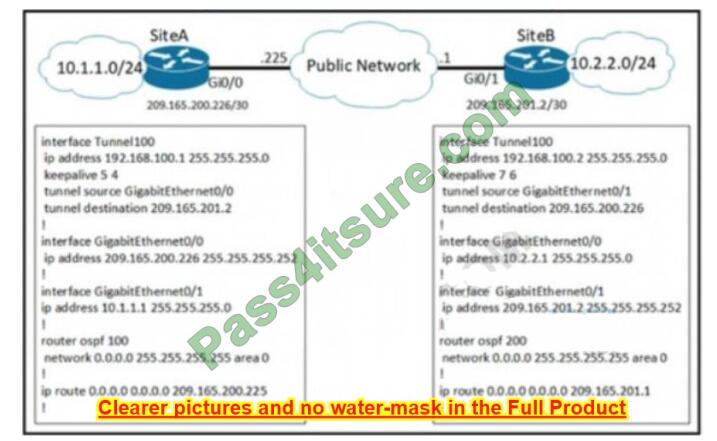
A. The tunnel will be established and work as expected
B. The tunnel destination will be known via the tunnel interface
C. The tunnel keepalive is configured incorrectly because they must match on both sites
D. The default MTU of the tunnel interface is 1500 bytes.
Correct Answer: B
NEW QUESTION 12
DRAG DROP
Drag and drop the wireless elements on the left to their definitions on the right.
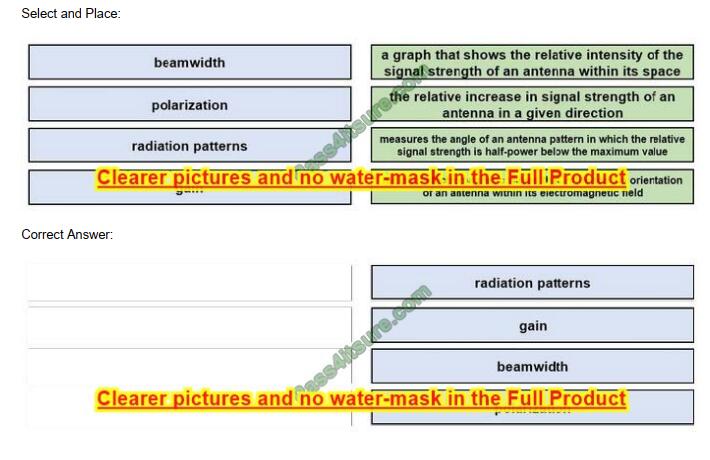
NEW QUESTION 13
In a Cisco SD-Access wireless architecture, which device manages endpoint ID to Edge Node bindings?
A. fabric control plane node
B. fabric wireless controller
C. fabric border node
D. fabric edge node.
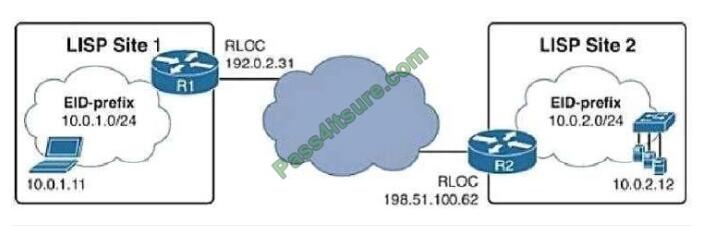
Correct Answer: A
SD-Access Wireless Architecture Control Plane Node Closer Look Fabric Control-Plane Node is based on a LISP Map
Server / Resolver Runs the LISP Endpoint ID Database to provide overlay reachability information
+
A simple Host Database, that tracks Endpoint ID to Edge Node bindings (RLOCs)
+
Host Database supports multiple types of Endpoint ID (EID), such as IPv4 /32, IPv6 /128*, or MAC/48
+
Receives prefix registrations from Edge Nodes for wired clients and from Fabric mode WLCs for wireless clients
+
Resolves lookup requests from FE to locate Endpoints
+
Updates Fabric Edge nodes, Border nodes with wireless client mobility, and RLOC information
Reference: https://www.ciscolive.com/c/dam/r/ciscolive/latam/docs/2018/pdf/BRKEWN-2020.pdf
Using the latest 350-401 dumps (r 9.27): https://www.pass4itsure.com/350-401.html makes it easy for you to pass the 350-401 exam.
