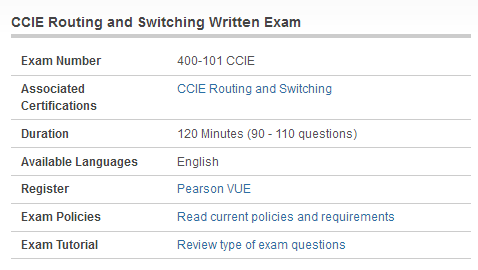
What is Cisco 400-101 dumps? The CCIE Routing and Switching Written Exam (400-101 CCIE Routing and Switching) exam is a 120 Minutes (90 – 110 questions) assessment in pass4itsure that is associated with the CCIE Routing and Switching certification.”CCIE Routing and Switching Written Exam” is the exam name of Pass4itsure Cisco 400-101 dumps test which designed to help candidates prepare for and pass the Cisco 400-101 exam. Helpful Cisco 400-101 dumps vce CCIE Routing and Switching exam V5.1 video training online. It is famous for the most comprehensive and updated by the highest rate https://www.pass4itsure.com/400-101.html dumps. It also can save time and effort.
[2017 New Updated Pass4itsure 400-101 Dumps From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWczJDVzl1SUJLWms
[2017 New Updated Pass4itsure 70-696 Dumps From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWWkMxQnU0WEtjbXM
Pass4itsure Latest and Most Accurate Cisco 400-101 Dumps Exam Q&As:
7.Which technology does OSPFv3 use to authenticate packets
A. SHA256
B. 3DES
C. AES
D. IPsec
400-101 exam Correct Answer: D
Explanation
Explanation/Reference:
8.Which two statements about the OSPF two-way neighbor state are true? (Choose two)
A. It is valid only on NBMA networks.